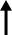|
| Screenshot of the Korean East-West Mind Science Association website after being compromised by a hacker group that calls itself 'Dawn Cavalry." Korea Times file |
Group attacks 12 South Korean research, academic agencies
By Jack Lau
A foreign hacker group, apparently a Chinese one, attacked the websites of a dozen mostly research and academic institutions in South Korea over the Lunar New Year holiday, the country's cyber-safety agency said on Wednesday.
The hacker group, which identifies itself as Dawn Cavalry, said on its public channel on messaging app Telegram that its next target is the Korea Internet and Security Agency (KISA), which is the first government agency to be identified as a target of the group's cyberattacks.
"The next target is KISA," a Dawn Cavalry administrator wrote in a message in Chinese and English on Telegram. "The specific invasion list is waiting for the official reply from South Korea."
"So far, the South Korean government has reported breaches from only 12 agencies, but I've deleted more databases and websites than that."
Some of the compromised websites have recovered and are functioning normally, but most are still reeling from the attack and could not be accessed on Wednesday afternoon. Hacked homepages feature a message of the hacker group's logo and name in Chinese characters and English. Underneath them is a phrase that reads, "We Declare an Invasion of the South Korean Internet."
KISA told The Korea Times that it cannot confirm if the hackers were Chinese nationals and whether they were state-sponsored. Dawn Cavalry wrote in its Telegram channel in English and simplified Chinese, which is used mainly in mainland China.
The Korea Research Institute for Construction Policy (RICON) became Dawn Cavalry's first target, KISA said. The hacker group said Friday on its website that it had leaked the personal information of the institute's staff members and research fellows, including their names, email addresses and job titles. Its website remained inaccessible.
Two days later, on Tuesday, 11 other South Korean academic institutions sustained similar cyberattacks by the group, including The Korea Association for Education and The Korean East-West Mind Science Association, a non-profit group dedicated to the rehabilitation of visually impaired people, and The Korean Society for the Study of Educational Principles.
The hackers broke into their web servers and replaced the website hosted on them with their messages written in Korean.
"We will continue to hack Korea's public and government networks, and looking forward to our next move, we will hack a wide range of internal South Korean networks," said the message, written in Korean, set against a background inspired by The Matrix's digital rain. "Yes, we are back."
Most of these institutions have websites that do not support encrypted data transfers from the user and the web server, making them vulnerable to cyberattacks and eavesdropping of private information.
The source code of the website included hidden comments written in simplified Chinese, which is used primarily in mainland China. The same code could be found in Chinese developer blogs and tutorials for creating the Matrix-inspired background.
"Our team is an independent team. Our team will use South Korea as a training ground for members, and every one of them will take part in actions invading South Korea," Dawn Cavalry said on Telegram. The group's name apparently refers to the ancient Chinese military contingent.
Only the administrator can upload posts on the Dawn Cavalry channel, and its subscribers can leave only comments. As of Wednesday, the channel had over 500 subscribers.
Regarding the question of how South Korea became a target, the administrator wrote that they were annoyed by some streaming stars from Korea.
The group warned on its website on Jan. 7 that its actions against South Korea would cause "data leaks to happen for a long time."
"An investigation into the cyberattack is underway," a KISA staffer said on condition of anonymity. "We find it difficult to identify who those hackers are and why they targeted South Korea, and so on, mainly because the cyberattack occurred during the holiday and many of our inquiries were not answered yet."
Jack Lau is a reporter with the South China Morning Post. He is currently based in Seoul, writing for both The Korea Times and the South China Morning Post under an exchange program.
 Subscribe
Subscribe E-Paper
E-Paper